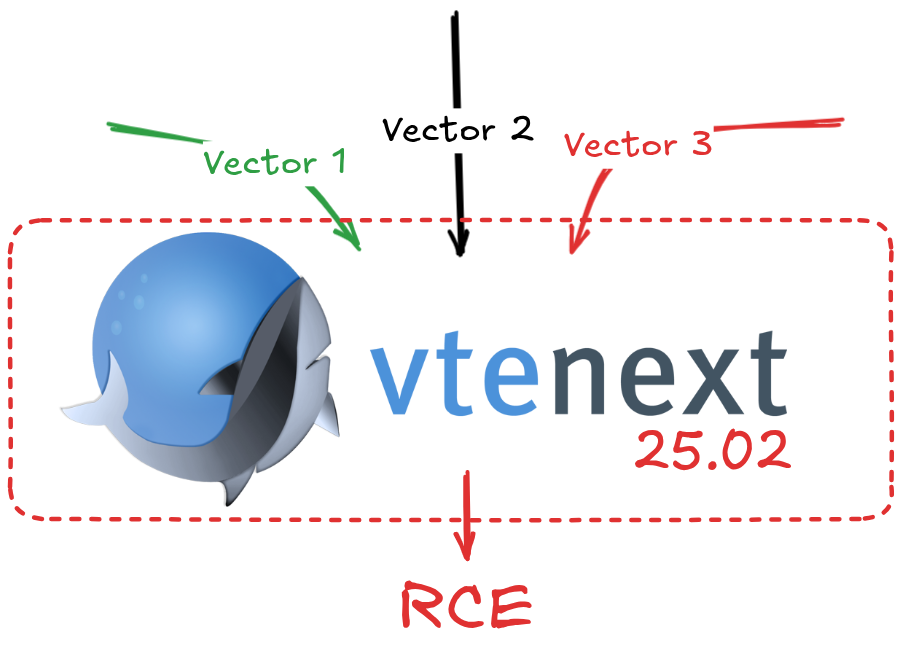
Vtenext 25.02 vulnerability research
Multiple vulnerabilities in vtenext 25.02.1 and prior versions allow unauthenticated attackers to bypass authentication through three separate vectors, ultimately leading to remote code execution on the underlying server.
Vtenext 25.02 vulnerability research
Summary
- Product
- VTENEXT CRM
- Vendor
- vtenext
- Severity
- Critical
- Impact
- Authentication Bypass and Remote Code Execution
- Affected Version(s)
- 25.02* and below
- Tested Version(s)
- 20.04, 24.02, 25.02, 25.02.1
- First Patched Version
- 25.02.2
Abstract
Multiple vulnerabilities in vtenext 25.02.1 and prior versions allow unauthenticated attackers to bypass authentication through three separate vectors, ultimately leading to remote code execution on the underlying server.
You can read the full article on the SicuraNext blog.
Disclosure Timeline
Please refer to the disclosure policy page for further details about the disclosure policy adopted by 0xbro.
- 28/05/2025: Contacted vtenext for the first time through various communication channels, but did not receive any response.
- 05/06/2025: Contacted vtenext for the second time, but didn’t receive any response again.
- 09/06/2025: Submitted CVE Request 1879483 to MITRE (still awaiting official CVEs).
- 13/07/2025: Attempted to contact the developers of vtenext via a direct channel on LinkedIn, but without success.
- 24/07/2025: Vendor released version 25.02.1 containing a silent patch for the Arbitrary Password Reset vulnerability.
- 12/08/2025: Full disclosure, since a patch exists and the grace period has expired.
- ??/08/2025: Vendor released version 25.02.2 containing a patch for the other vulnerabilities.
- 04/09/2025: Following a call with the vtenext team, it was decided to reduce the technical details of the vulnerabilities to give users time to update to the latest version and the team time to patch the remaining vulnerabilities.
This post is licensed under
CC BY 4.0
by the author.